Proton blog

- Proton news
- Product updates
- Proton Pass

- Privacy guides
If you’re comparing different password managers or researching password
security, you’ll quickly run into terms like hashing and salting. While these
terms might sound like steps you take to make breakfast potatoes, they’re
actually processes that ar

People often choose to remove their personal information from the internet due
to privacy and security concerns. For example, oversharing on social media can
expose you to phishing attacks, identity theft, and cyberstalking.
Plus, your data is highl

It’s been roughly two months since the European Union’s Digital Markets Act
(DMA), which aims to restore competition and fairness to the internet, came into
effect for Big Tech monopolies. Since then, Google has done precisely nothing to
comply with

- Product updates
- Proton Pass
Today, we’re excited to announce the launch of the Proton Pass macOS app and the
Proton Pass Linux app. One of the most popular requests from the Proton
community was a standalone desktop app, which is now available on every major
platform — Windows,

- Product updates
- Proton Pass
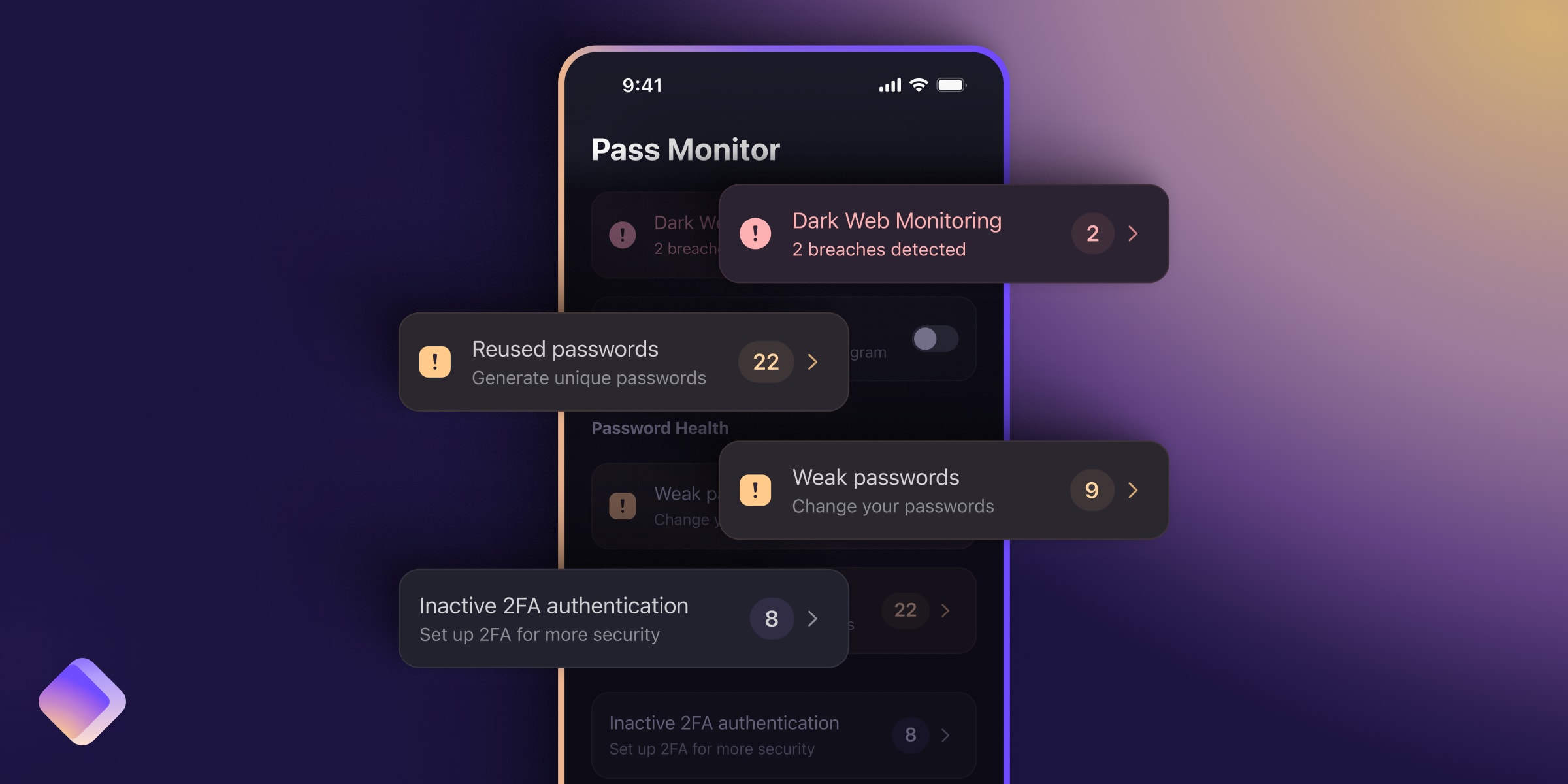
Data breaches are increasingly common. Whenever you sign up for an online
service, you provide it with personal information that’s valuable to hackers,
such as email addresses, passwords, phone numbers, and more. Unfortunately, many
online services f

- Product updates
- Proton Mail
Your email address is your online identity, and you share it whenever you create
a new account for an online service. While this offers convenience, it also
leaves your identity exposed if hackers manage to breach the services you use.
Data breaches

- Proton news
Every year, we send a survey to the Proton community asking for your feedback
and ideas. We then use that information to guide our future plans. This year, we
received thousands of responses, giving us insight into what you expect from
us.
As one o

- Proton news
At Proton, we have always been highly disciplined, focusing on how to best
sustain our mission over time. This job is incredibly difficult. Everything we
create always takes longer and is more complex than it would be if we did it
without focusing on

In February 2024, media reported that Indian authorities may decide to block
Proton Mail. Proton Mail is still available in India despite any reports
suggesting otherwise.
In response to hoax bomb threats that were sent through Proton Mail, some
me

When you use the internet at home, connected to everything from fitness
equipment to game consoles, smartphones, and laptops, marketing companies could
be watching you with a tiny piece of surveillance tech you might not even know
about.
We’re talki

The email addresses and other sensitive information of 918 British MPs, members
of the European Parliament, and French deputies and senators have been leaked to
dark web marketplaces where data is illegally bought and sold. As part of our
investigati

Section 702 of the Foreign Intelligence Surveillance Act has become notorious as
the legal justification allowing federal agencies like the NSA, CIA, and FBI to
perform warrantless wiretaps, which sweep up the data of hundreds of thousands
of US citi

- Privacy guides
If you’re comparing different password managers or researching password
security, you’ll quickly run into terms like hashing and salting. While these
terms might sound like steps you take to make breakfast potatoes, they’re
actually processes that ar

People often choose to remove their personal information from the internet due
to privacy and security concerns. For example, oversharing on social media can
expose you to phishing attacks, identity theft, and cyberstalking.
Plus, your data is highl

- Privacy guides
Hackers use various methods to crack passwords, and one of them is the rainbow
table attack. In certain cases, this method can be faster than dictionary
attacks or credential stuffing.
In this article, we explore how rainbow table attacks work and d

It’s been roughly two months since the European Union’s Digital Markets Act
(DMA), which aims to restore competition and fairness to the internet, came into
effect for Big Tech monopolies. Since then, Google has done precisely nothing to
comply with

We recently announced that Proton Pass now supports passkeys for everyone across
all devices.
Universal compatibility is a unique approach to implementing passkeys,
unfortunately. Even though passkeys were developed by the FIDO Alliance and the
Worl

If there were still doubts over whether Apple is an abusive monopolist, they
were emphatically dismissed this week. Apple’s new app store policy that it
claims will bring it into compliance with Europe’s Digital Markets Act is a
textbook case of mali

Today we’re announcing enhancements to our business plans, further enriching our
commitment to delivering the best privacy experience for businesses. These
upgrades will help us continue expanding our feature suite for organizations,
while giving mor

- For business
Ensuring HIPAA compliance is crucial for any healthcare business that handles
sensitive patient information. Failing to use HIPAA-compliant services, such as
email, can result in severe consequences, including hefty fines and legal
repercussions.
If

Secure, seamless communication is the foundation of every business. As more
organizations secure their data with Proton, we’ve dramatically expanded our
ecosystem with new products and services, from our password manager to Dark Web
Monitoring for cr


