These days, email breaches are becoming increasingly common for enterprises. There are however reliable ways to prevent email breaches, or reduce their impact.
It should really come as no surprise that email hacks are on the rise. As businesses go digital, email data is becoming increasingly valuable for hackers. While the trending topic this week is the Deloitte hack(new window), this is only the latest in a long string of email hacks. Other past victims include Sony Pictures(new window), the Democratic National Committee(new window), and Yahoo Mail(new window).
When confronted with this trend, one might think that email hacks are inevitable, and that any organization can be hacked sooner or later. This in fact is the correct thinking, and should be the mindset security professionals have when thinking about data breaches. If even the NSA was breached(new window), it’s safe to assume that every organization can be hacked.
While it may feel that there is no hope for cybersecurity, this realization actually provides remarkable clarity for how we should protect data in an increasingly dangerous environment. What is required is tackling the issue on a different level and viewing data security from a different perspective.
If we are forced to accept that hacks cannot be prevented, then the security emphasis is no longer on keeping the intruder out, but minimizing the damage after security systems have been breached. When it comes to email, there are actually several concrete steps which can be taken to greatly reduce the risk associated with an email hack.
1. Use email with end-to-end encryption
End-to-end encryption is a technology which encrypts all data before it is sent to a server, using an encryption key that the server does not possess. The security advantages of this approach are clear.
If all email is encrypted before it arrives at the server, then a breach of the email server will not cause sensitive email contents and attachments to be leaked. It is important to note that there is a major difference between encryption and end-to-end encryption.
With end-to-end encryption, the server does not have access to the decryption keys. This means there is no way for a hacker with access to the email server to decrypt the encrypted emails because the server itself does not possess the decryption keys.
In classical encryption schemes, the decryption keys are available to the server, which is akin to putting the padlock and the key in the same place, which largely negates the advantage of having a lock in the first place.
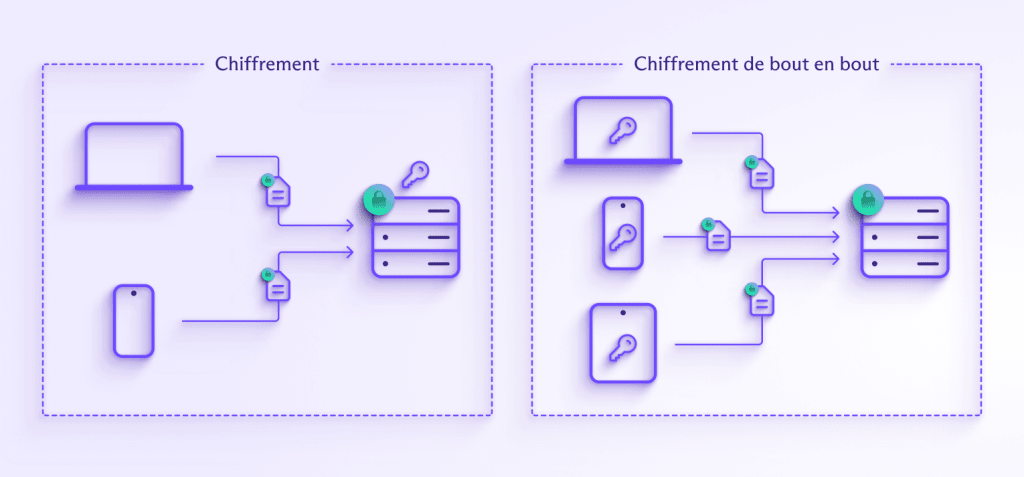
In email systems with end-to-end encryption, the decryption keys are accessible only to client systems, and each client has a different decryption key, making a large scale email compromise difficult to accomplish.
The risk is significantly reduced because compromising the email server does not leak any email contents. Furthermore, in the event that a client device is hacked, only a single encryption key is compromised, and not the keys to the whole system, since each client has a different encryption key.
There are several ways for an organization to implement end-to-end encryption. One way is to train all employees to use PGP, a system for end-to-end email encryption. The more modern way is to use an email provider such as Proton Mail that already has PGP built-in. The advantage of using Proton Mail is that the encryption is done automatically and is fully transparent to the user, meaning that no end-user training or complex key management is required.
This is indeed the approach that many companies with sensitive security needs have selected, and Proton Mail is used today by many legal, healthcare, finance, and media organizations. Prominent media outlets that now use Proton Mail to protect confidential sources include Huffington Post(new window), Foreign Policy(new window) magazine, NJ.com(new window), and many others.
Earlier this year, Proton Mail became HIPAA compliant(new window) and enterprise ready, and can now serve as a drop-in alternative to Microsoft Exchange, Microsoft 365, or Google Workplace. End-to-end encryption by itself however, is not sufficient for full protection against email hacks.
2. Protect or restrict administrator accounts
While end-to-end encryption will protect from an email server breach, it offers limited protection against a compromise of an administrator account.
In general, administrators can be compromised in several ways, including incidents of insider threat, carelessness, or even targeted hacking via phishing(new window) campaigns. In most organizations, if an email administrator is compromised, all email accounts can be breached.
To guard against this threat, we recommend strongly protecting or restricting administrator accounts. Some ways to protect administrator accounts include the following:
- Only allow logging into administrator accounts from certain secured computers which are not used for other purposes to reduce the risk of infection.
- Never remove the secured computers from company premises to reduce the risk of system theft. Make sure this machine uses full disk encryption.
- Always enable two factor authentication on administrator accounts (this is supported by Proton Mail).
- Do not store administrator passwords on systems with network access. Keep them instead on paper or on systems which are air-gapped and cannot connect to the Internet. Do not permit administrator passwords to be removed from company premises by administrators.
- Enforce the two-person rule, where the administrator password and the second factor device are kept by two separate people.
These steps can significantly reduce the attack surface that your organization needs to defend against. If it is not feasible to so heavily defend administrator accounts, the next best thing you can do is to heavily restrict administrator accounts.
Proton’s secure business email(new window) provides a built in way to restrict administrator accounts by supporting two types of user accounts. When you use Proton Mail for your organization, accounts can be designated as “private”. An account that is set to “private” has additional protection in that the contents of that account are unreadable to email administrators.
Even if an administrator account is compromised, the contents of “private” accounts remain safe. Therefore, highly sensitive accounts (like accounts used by C-level executives or HR) can be kept secure from rogue or compromised administrators.
Of course, the best approach is to avoid having a compromised administrator in the first place, which brings us to the third step to protect your organization from email hacks.
3. Protect end-users through good policies and training
Security is only as good as the weakest link, and even if you have strong technical security from Proton Mail’s end-to-end encryption, the human risk will always remain.
This must be mitigated through a combination of policies and training. An example of a policy decision which can improve organizational security is making two-factor authentication mandatory, which is something that we do in our organization.
Training is equally important. Within our organization, regardless of the role somebody is hired for, on the first day on the job, we provide them a detailed security guide which employees are required to read and understand.
This guide also includes a list of recommended software from vendors who are known to be secure. We also patch quickly and religiously.
Training should also be combined with technical measures. Today, spear-phishing campaigns via email poses one of the most dangerous threat vectors to organizations.
Phishing campaigns have become so sophisticated that even experienced administrators can be compromised. In order to combat this, Proton Mail includes a number of advanced anti-(new window)phishing(new window) features(new window) which are not found in any other email service. This gives organizations using Proton Mail a much better chance of resisting sophisticated phishing attacks.
Final Thoughts
Security is difficult, and if history has shown us anything, it is that there is no such thing as 100% security. This means we need to fundamentally re-tool how organizations approach cybersecurity.
Technological advances such as easy-to-use end-to-end encryption make it possible to still have good security in a world where we assume everybody is going to get hacked. By taking the security measures outlined here, you can ensure that your organization is better prepared for the riskier world that lies ahead.
You can get a free secure email account from Proton Mail here.
We also provide a free VPN service(new window).
Proton Mail and Proton VPN are funded by community contributions. If you would like to support our development efforts, you can upgrade to a paid plan(new window). Thank you for your support!