The latest version of the Proton Mail webapp includes three new features for improved security and convenience.
Proton Mail version 3.16 now offers elliptic curve cryptography, an optional link confirmation warning to guard against phishing attacks, and an “undo move” feature for those moments you accidentally send an email to the trash or the wrong folder.
Elliptic curve cryptography (ECC)
Proton Mail joins a growing number of tech services offering elliptic curve cryptography. ECC is a more modern alternative to RSA that allows you to use smaller keys while accomplishing the same level of security. If you choose to upgrade your mailbox to the new ECC keys, you may notice slightly shorter encryption times.
Because of the unique nature of elliptic curves, ECC saves processing power (allowing you to log in, load, and send emails faster), memory (freeing up space for other apps), and energy (longer battery life), especially on mobile phones.
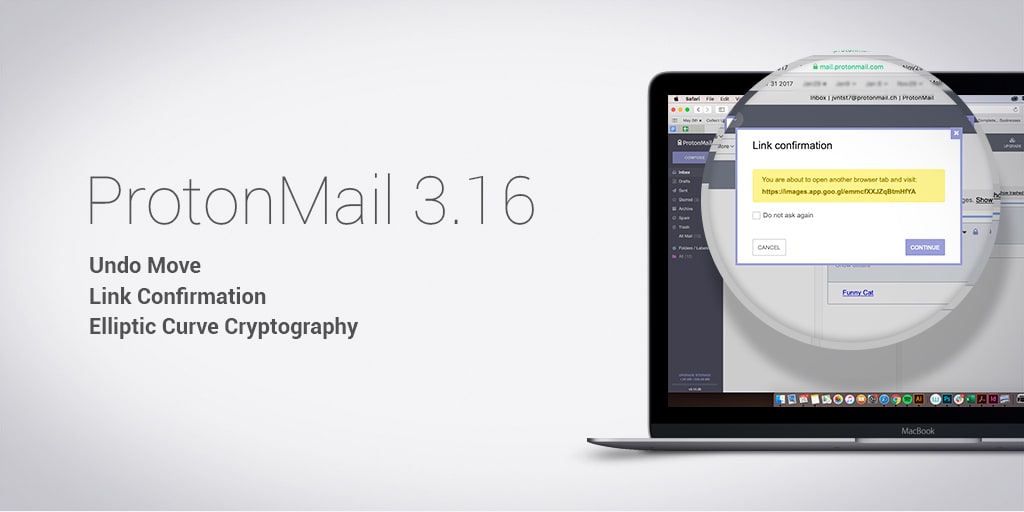
Link confirmation
Link confirmation is a new security feature in Proton Mail version 3.16 that can help you identify possible phishing attacks. While link confirmation is enabled, whenever you click on a link in an email, a window first pops up asking whether you’re sure you would like to visit the URL. Phishing emails (new window)are the most common method for hackers to deliver malware or gain access to your account. Link confirmation helps you avoid accidentally landing on a malicious webpage.
You can learn how to enable and disable link confirmation(new window) in the webapp, Android, and iOS.(new window)
Undo move
Here’s something that’s mildly annoying: when you hit “move to trash” but you meant to click on “move to archive”. We’ve added a new undo move feature for just such occasions.
Instead of hunting for it in the incorrect folder and moving it, it’s now easy to undo the action by clicking on the UNDO button at the top of your mailbox. The button works when you send an email to any folder and restores it to the previous folder. For example, if you move an email from your Spam folder to your Inbox, you can quickly move it back to Spam. But click fast: the button disappears after a few seconds.
We’re excited about these new updates and we look forward to hearing your feedback!
Best Regards,
The Proton Mail Team
Get a free secure email account from Proton Mail.
We also provide a free VPN service(new window) to protect your privacy.
Proton Mail and Proton VPN are funded by community contributions. If you would like to support our development efforts, you can upgrade to a paid plan.
Thank you for your support.