UPDATE January 11, 2023: We added statistics about the number of trackers in emails that are blocked by Proton Mail.
Big Tech wants all of your data, and they’re constantly looking for new ways to collect it from you. Even if you use a secure email service that encrypts the content of your emails, like Proton Mail, marketing companies insert trackers into emails and newsletters they send you that can see:
- When you opened an email
- Where you were located when you opened it
- What device you used to read it
At Proton, we believe you should be able to read your emails without worrying about who is spying on you or what they will do with that information.
With that goal in mind, we introduced enhanced tracking protection on the Proton Mail web app in January 2022. This was a major step forward for your privacy. We block tens of millions of trackers every month, and we’ve found that nearly 50% of all emails contain some kind of tracker. That means there are over 166 billion emails sent with trackers every day.
Today, we’re excited to let more of you enjoy a safer email experience. We’re introducing improved protection against email trackers on the web and, for the first time, on the Proton Mail app for iPhone and iPad. The introduction of enhanced tracking protection on our iPhone and iPad apps allows us to block 46% more trackers.
Protecting you from more tracking attempts
Email tracking is a form of digital surveillance that typically involves embedding tracking pixels in your emails’ images that can track your mail activity. Most senders want to know if or when you open their emails and build a profile on you without your consent.
When we launched our tracking protection feature, we focused on preventing tracking attempts. The Proton Mail web app already protects your privacy by:
- Blocking known trackers commonly found in newsletters and promotional emails, preventing senders from spying on you.
- Hiding your IP address by loading every remote image inside your emails using our own servers instead of your device, so your location and the ISP you use remain private.
Our latest improvement prevents trackers from knowing when you open an email. From now on, Proton Mail will pre-load remote images for you as soon as an email is delivered rather than when you open it. Images are then cached, allowing you to re-open the email privately without needing to load images again.
This works for non-end-to-end encrypted emails, which include most newsletters and promotional emails that typically include trackers.
It effectively makes any analysis of if or when you opened an email unusable. To marketers, all emails sent to Proton Mail addresses will always appear as though they’ve been opened as soon as they’re delivered.
You don’t need to do anything to benefit from these added defenses against tracking. They’ll run automatically in the background as part of tracking protection.
Enjoy a safer email experience on iPhone and iPad
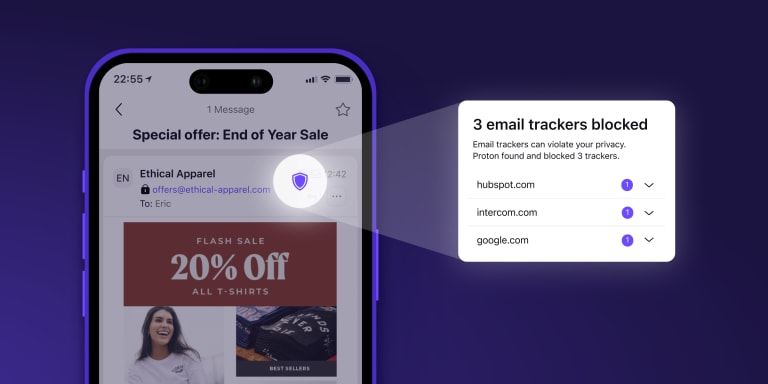
You should be able to read your emails privately, regardless of what device you use. That’s why we’ll also be making enhanced tracking protection available on the Proton Mail app for iPhone and iPad in the coming weeks.
With tracking protection on your iPhone:
- You’re protected by default when you read your emails.
- You can tap the shield icon to view which email trackers were blocked.
- Images are pre-loaded immediately to protect your privacy.
Making email better for everyone
When we first launched enhanced tracking protection, we noticed that email senders make it difficult for you to view their emails without loading images. They force you to choose between your privacy and convenience.
With our improved tracking protection, you don’t have to choose. We load remote images while keeping your email activity private.

Now that you can view images in your emails without being spied on, we introduced two new changes to our default settings:
- Remote images are now automatically displayed if you use a supported platform (web, and soon iPhone/iPad).
- You can now choose different image settings per app. For example, you can automatically display remote images in your emails on the web and turn this feature off on your iPhone.
No trackers, just your emails — the way it should be
We are focusing our efforts on bringing tracking protection to the Proton Mail app for iPhone and iPad. If you have questions about using tracker protection, read our support articles on tracking protection and images in Proton Mail.
We’re happy we can help carve out another corner where you read your messages and reflect in peace. This is the privacy we’re working to deliver to the rest of your internet experience.
Thank you for your support. You’re helping us build a better internet that’s private by default.