Below are the release notes for Version 3.2 of the Proton Mail secure email web client. This release bring several enhancements including improved spam filtering(new window) and improvements to make labels more efficient and easy to use. We are now actively working on a future 3.x release which will contain a complete filters functionality which will allow the creation of custom filters to be applied automatically to incoming emails. As usual, if you encounter any bugs with this version, please let us know via the report bug functionality, or through our support page.
Proton Mail does not show advertisements or abuse your privacy for revenue. Paid accounts are our only source of funding. Please consider upgrading to a Proton Mail Plus(new window) account so that we can continue to operate the service and fund the development of more features.
New Features Summary
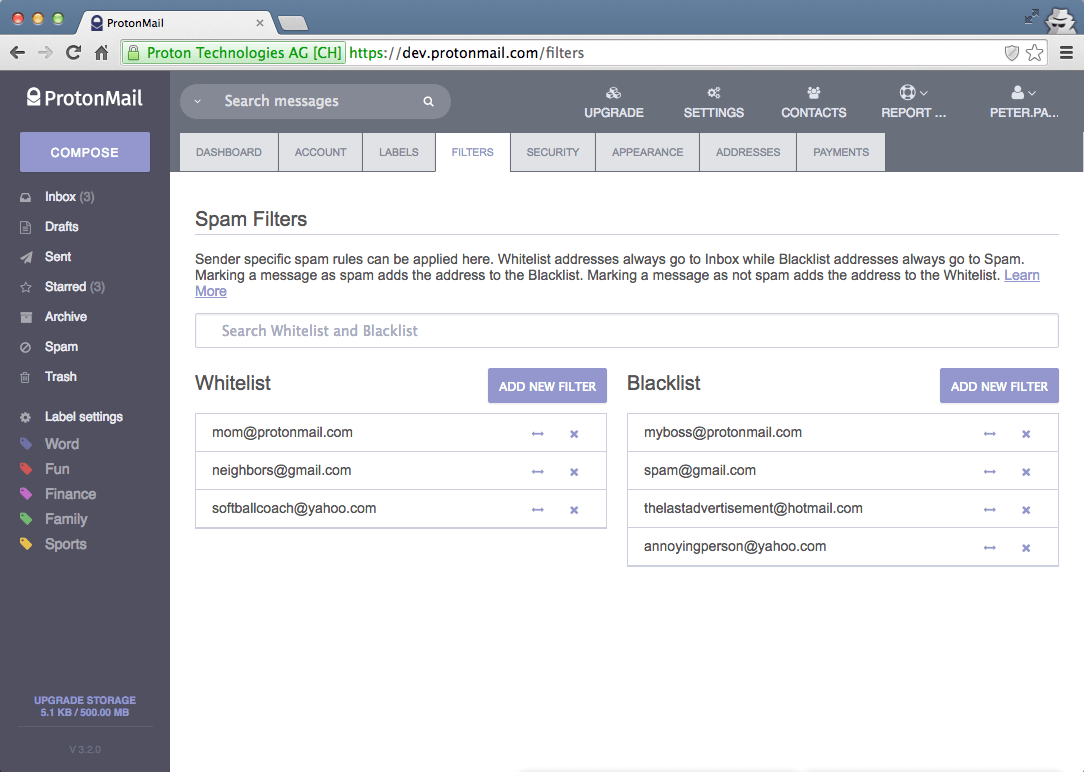
Custom Spam Filters
Spam is the least desirable side effect of owning an email account. Spam filtering is a particularly challenging problem when it comes to end-to-end encrypted email because we don’t have the ability to read emails. Proton Mail utilizes a number of techniques to automatically detect and filter spam messages. However, when it comes to spam, there isn’t a one size fits all solution, and it may be some necessary fine tuning on a per account basis to get the filtering just right. With Spam Filters, you can now create your own unique whitelist and blacklist to ensure your mail is automatically delivered into your inbox and spam folder correctly. You can learn more about this feature here.
Improved Labels
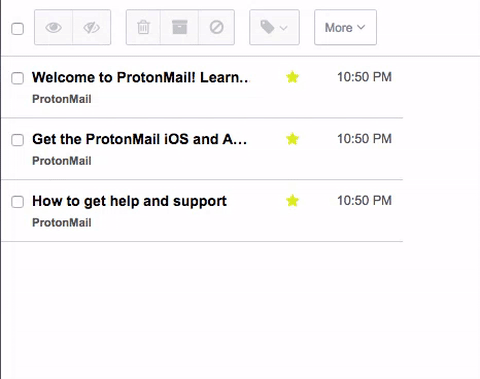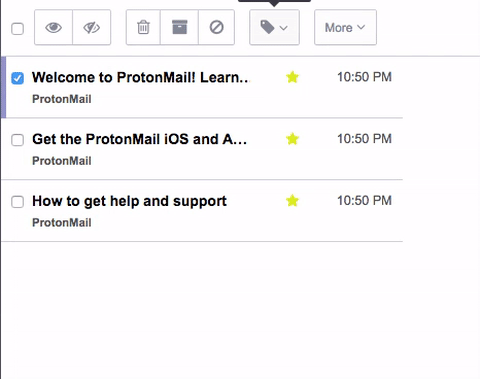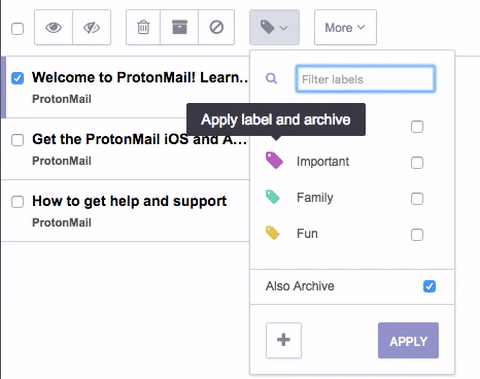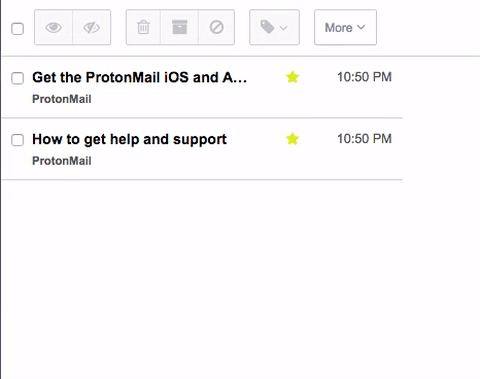
In version 3.2, we also improved labels to make them easier to use. The first improvement is that in the labels menu, the state of the ‘Also archive’ is now saved. Thus, for users that always use the Also archive functionality, there is no need to re-check it every single time.
Secondly, we added a quick label functionality. If you click on the left side icons shown above, you can directly apply a single label without clicking the check boxes or clicking apply. This saves one click when applying a label. If Also archive is turned on, using the quick label functionality will also archive that conversation.
Version 3.2 Release Notes
New Features
- New tab in Settings to set Spam Filters
- New drop down labels
- Spoof warning in body of messages that may have been spoofed
Bug Fixes
- Many fixes and features to improve Proton Mail Web view and Mobile view
Improvements
- New composer (faster and more stable)
Known Issues
- PGP key export/import functionality still missing in version 3.x, will be done for a future release.
- Some mobile responsive issues remain
Please report bugs here: https://proton.me/support