Learn what PGP encryption is, how it works, and the simplest way to secure your emails with PGP.
When Edward Snowden secretly communicated(new window) his surveillance revelations to journalists in 2013, he used PGP encryption. Over the years, thousands around the world have turned to PGP to protect themselves online, from whistleblowers to ordinary people defending their right to privacy.
We explain all you need to know about PGP and how to easily secure your communications with this robust encryption method.
What is PGP encryption?
What does PGP stand for?
What is OpenPGP?
How does PGP work?
Public-key encryption
Public-key and symmetric encryption
Why does PGP use two encryption methods?
Digital signatures
Address verification
OpenPGP CA
How secure is PGP encryption?
How to use PGP encryption
Proton Mail
Third-party PGP plugins
Other PGP clients
Easy PGP email encryption
What is PGP encryption?
PGP is an encryption method that lets you communicate privately online. It’s commonly used to encrypt emails, but it can also be used to encrypt files and other data.
When you send an email using PGP, the message is converted into unreadable ciphertext on your device before it passes over the internet. Only the recipient has the key to convert the text back into a readable message on their device.
PGP is also used for authentication. By providing a way to digitally “sign” encrypted emails, PGP lets you check that the message is from the person claiming to be the sender and verify that it wasn’t tampered with in transit.
What does PGP stand for?
PGP stands for “Pretty Good Privacy”. When PGP was created in the 1990s, the publicly available cryptography was limited, and PGP gave you privacy that was “pretty good”. Since then, as cryptography has advanced, several factors have helped PGP become one of the main standards for email encryption.
First, PGP is now highly secure if implemented correctly with strong encryption. Send a message using PGP, and no one can intercept and read it in transit. That’s why privacy-focused email providers like Proton Mail use PGP for their end-to-end encryption.
Second, PGP uses both symmetric-key(new window) and public-key(new window) encryption, as we explain below. This increases security and ease of use because you can send an encrypted message to someone without sharing a secret key in advance.
Third, PGP evolved into OpenPGP(new window), an open standard that the cryptographic community is constantly improving. At Proton, we not only use OpenPGP, we also help to maintain and develop it.
What is OpenPGP?
OpenPGP is an open standard of PGP encryption that’s free for public use.
Invented by software engineer Phil Zimmermann as freeware in 1991, PGP encryption later became proprietary software and is now owned by Symantec.
But Zimmermann also shared the message format used by PGP with the wider community. Based on this, the OpenPGP standard was created in 1997, enabling anyone to write implementations that are compatible and interoperable with other software that uses OpenPGP.
Several OpenPGP-compliant “libraries” have been created to help programmers implement PGP encryption in their apps. At Proton, we maintain two of these libraries:
- OpenPGP.js(new window) uses the JavaScript programming language used in our web app. OpenPGP.js is one of the world’s most widely used OpenPGP libraries.
- GopenPGP(new window) uses the Go language (also known as Golang) used in our mobile and desktop apps. We started this project to make it easier for mobile and desktop developers to use OpenPGP encryption in their apps.
How does PGP work?
PGP combines public-key encryption(new window), also known as asymmetric encryption, and symmetric-key encryption(new window). Here’s how PGP’s public-key encryption works in simple terms.
Public-key encryption
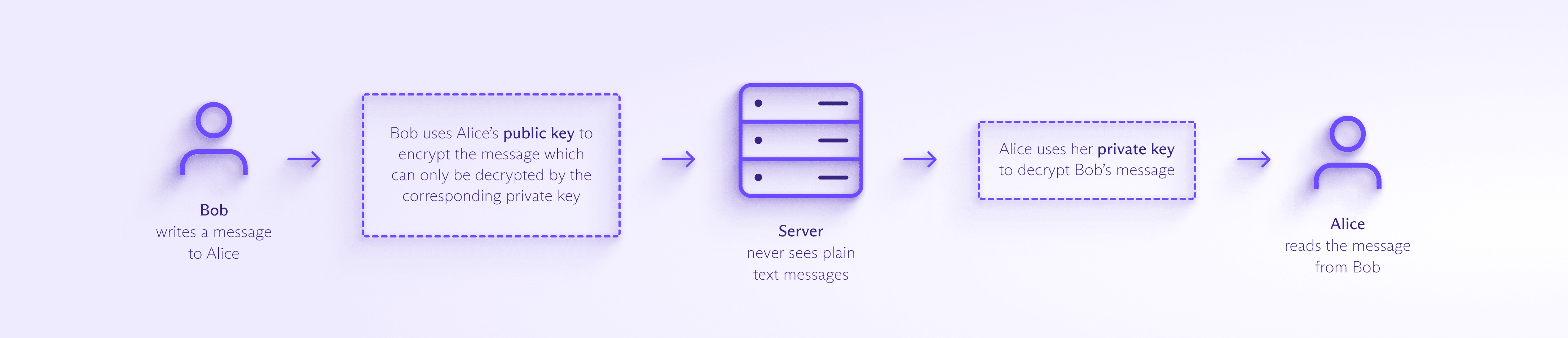
Imagine Bob wants to say hello to his friend Alice privately. PGP generates a public key and a private key for Alice, known as a key pair. These public and private keys are strings of bytes representing numbers that are mathematically related.
Alice can share her public key with anyone. Then anyone can use it to send her encrypted messages. But only Alice has the private key that can decrypt those messages.
So when Bob writes to Alice:
1. Bob uses Alice’s public key to encrypt his message, turning “Hello, Alice!” into ciphertext(new window) – seemingly random characters that can’t be read.
2. Bob sends the message. Anyone who tries to read it in transit, like email providers, spies, or hackers, will only see this unreadable ciphertext.
3. Alice receives the message and uses her private key to decrypt the message into readable plaintext(new window).
4. To reply, Alice repeats the process using Bob’s public key. Only Bob can read it by decrypting it with his private key.
Public-key and symmetric encryption
PGP combines public-key encryption with another method of encryption: symmetric encryption, which is when only one key is used to encrypt and decrypt messages.
Here’s how it works when Bob writes to Alice:
1. PGP creates a single-use session key(new window) to encrypt Bob’s message. The session key is symmetric because both Bob and Alice can use it to encrypt or decrypt the message.
2. PGP then encrypts Bob’s session key using Alice’s public key, and the encrypted message and encrypted session key are both sent to Alice.
3. Alice uses her private key to decrypt the session key. She then uses the decrypted session key to decrypt and read Bob’s message.

Why does PGP use two encryption methods?
PGP combines public-key encryption with symmetric encryption for two main reasons.
First, public-key cryptography is much slower than symmetric cryptography, especially for large messages. Encrypting and decrypting large emails or files using the public key directly would take a lot of time and computing power. Instead, PGP uses public-key cryptography only to encrypt the session key, so it doesn’t take long or use much computing power at all.
Second, if you used symmetric cryptography without public-key cryptography, you would need to find a way to share the session key with the recipient. Share the key unencrypted, and anyone who intercepted it could read it and decrypt the whole message. And sharing the session key via another encrypted channel or in person is impractical for online communications.
Therefore, PGP combines the efficiency of symmetric encryption with the convenience of public keys that anyone can use.
Digital signatures
PGP also includes a system of digital signatures to verify the sender’s identity. A digital signature proves to the recipient that an attacker has not manipulated the message or the sender. If the PGP signature is valid, you can trust the authenticity of the message.
PGP signs an email by creating a unique number (the digital signature) using a combination of the sender’s private key and a mathematical redux (known as a message digest) of the plaintext message. This signature can then be verified using the public key of the sender. If either the public key or the message is altered, the signature is invalid.
Learn more about digital signatures
Address verification
Digital signatures help mitigate sophisticated attacks, but how can a sender know that the public key they’re using belongs to the person they think it does? After all, anyone can create a key and claim it belongs to a specific email address. An attacker could replace your public key with one of their own, giving them access to any messages encrypted with that key.
Public-key encryption systems like S/MIME (available for paid Gmail and Outlook accounts) rely solely on a centralized system of certificate authorities (CA)(new window) to verify the ownership of public keys. The downside with CAs is that they’re third-party points of failure that could be compromised.
In contrast, PGP has a decentralized trust model where users can verify the identity of other users.
In Proton Mail, you can mark a public key as trusted for each of your contacts, a process known as “key pinning”. When that public key changes, you get a warning that sender verification has failed so that you can ask your contact whether they have indeed changed their public key.
If the sender’s identity is verified, you’ll see this lock symbol in the From address:

At Proton, we’re also developing a more automated system to verify public keys called Key Transparency. With Key Transparency, you’ll be able to automatically verify that you’re using the correct public keys without having to trust each of them manually.
OpenPGP CA
In addition to verifying individual keys, the OpenPGP community recently developed OpenPGP CA(new window), a system to verify the keys of email addresses under a given domain. This is especially useful for organizations to verify all the keys for their members more easily.
At Proton, we’ve created a certificate authority called ProtonCA so that other providers and users outside Proton can more easily verify the keys of our users.
How secure is PGP encryption?
PGP is a battle-tested standard and highly secure if implemented correctly with strong encryption keys. That’s why Edward Snowden used GPG(new window), which follows the OpenPGP standard, to relay his secrets in 2013.
As far as we know, even intelligence agencies like the NSA can’t crack PGP’s encryption(new window). Cryptography works, as Snowden once observed(new window).
PGP uses AES(new window) for symmetric encryption and ECC or RSA for public-key encryption, all considered highly secure. Combining symmetric and public-key encryption gives PGP an extra layer of security, together with digital signatures (explained above).
While PGP is a highly robust cryptographic method, it has several caveats in practice.
First, PGP is only as strong as the keys used to encrypt and encrypt the data. If the keys are weak or compromised, the encryption can be cracked. That’s why Proton Mail uses strong encryption: AES-256 for symmetric encryption and ECC (Curve25519), RSA-2048, or RSA-4096 for public-key encryption.
Second, PGP is only as secure as its implementation. As the infamous Efail vulnerability report showed, PGP won’t protect you if you use a flawed client.
Third, like most security systems, the weakest link in PGP’s security chain is the user. If you misplace your private key or your device or accounts are compromised by a phishing attack, PGP can’t save you.
How to use PGP encryption
PGP is notoriously complicated to use. Most people who aren’t tech savvy would never bother to learn how to use PGP, while those who know how to use it often don’t because it’s too tedious.
That’s why we created Proton Mail – to make encryption so easy anyone can use it. Here we’ll look at the three ways you can use PGP to send encrypted emails, starting with the simplest.
Proton Mail
The easiest way to send an end-to-end encrypted email with PGP is to use Proton Mail. With Proton Mail, PGP encryption is automatic and as easy to use as ordinary email.
If you’re writing to someone on Proton Mail, simply compose your email as usual and hit Send. Your email will be end-to-end encrypted, as the padlock in the To field shows.

If you want to send an end-to-end encrypted email to someone who isn’t on Proton Mail, the easiest way is to use a Password-protected Email.
Compose your message as usual and click the External encryption button (with the lock icon) to enter a password.
You can sign up for a free Proton Mail account in a couple of minutes and start sending PGP-encrypted emails immediately.
If you would like to generate and control your PGP keys manually, you can also use Proton Mail as your PGP client. With full PGP support, key management, address verification, and encrypted Proton Contacts, it’s a simple way to communicate with other PGP users with the convenience of Proton Mail.
Third-party PGP plugins
Another way to use PGP is to use a third-party plugin like Mailvelope(new window), a browser extension that allows you to use PGP with your webmail.
All encryption is handled locally on your computer, and your email provider doesn’t have access to your private key. Although third-party plugins make PGP a lot easier to use, they require some setting up and have several other downsides:
- They don’t work in browsers on mobile devices.
- They don’t encrypt email attachments automatically; you must encrypt them separately.
- Most don’t offer email client support, so if you use a desktop app like Outlook, Apple Mail, or Thunderbird, you won’t be able to encrypt your emails.
Other PGP clients
The final way to use PGP is to get an app or software that supports OpenPGP(new window). There’s a wide range of free and paid OpenPGP-compliant clients, but they typically require considerable technical knowledge to set up and maintain.
Apart from this challenge and inconvenience, you could risk your security if you don’t share or store your encryption keys correctly.
Easy PGP email encryption
Since its creation in 1991, PGP has developed into OpenPGP and become the most widely used standard for email encryption. When implemented correctly, PGP can provide genuine end-to-end encryption. Only you and the person you’re writing to can read your message.
Today, the OpenPGP standard is still being improved. A cryptographic refresh adding even more modern and secure algorithms is currently underway. Yet PGP remains difficult and tedious to use, even for tech-savvy security professionals.
That’s why we created Proton Mail, an email service as easy to use as ordinary email but with PGP built in. So anyone can send PGP-encrypted emails automatically out of the box — no technical knowledge required.
Sign up for a free Proton Mail account, and you can start sending PGP-encrypted emails immediately.
If you’re experienced with PGP and prefer to manage encryption keys yourself, get Proton Mail as your PGP client.
At Proton, our goal is to give everyone privacy and security online. Join us and protect your privacy with PGP.
PGP frequently asked questions
What does PGP stand for?
PGP stands for Pretty Good Privacy. While the name sounds like you’re settling for less-than-great privacy, it’s actually highly secure when correctly implemented for end-to-end encryption. Phil Zimmermann, the developer of PGP, named it after the grocery store Ralph’s Pretty Good Grocery in Garrison Keillor’s stories about the fictional town of Lake Wobegon.
What are PGP, OpenPGP, and GPG (GnuPG)?
PGP is an encryption method used to encrypt and authenticate emails. It can also be used to encrypt and decrypt other types of files. Invented by software engineer Phil Zimmermann in 1991, the original PGP is now proprietary software owned by Symantec.
OpenPGP, short for “Open Specification for Pretty Good Privacy”, is the free and open version of PGP. It’s the standard that allows companies like Proton Mail to make and distribute PGP-compatible products. Standardized in 1997, OpenPGP has since created a free environment for PGP encryption tools to thrive and compete with each other.
GPG (or GnuPG), short for GNU Privacy Guard, is free encryption software based on the OpenPGP standard. First released in 1999, it was originally developed as an alternative to Symantec’s suite of PGP encryption tools.
What is a PGP key?
PGP email encryption uses two types of keys known as a key pair:
- Your personal public key, also known as a certificate, which you share with others so they can encrypt the messages they send you
- Your personal private key, which you should never share as you use it to decrypt the encrypted messages you receive
PGP uses this key pair to encrypt and decrypt your emails and prevent anyone from intercepting and reading them. For details, see How does PGP work?








